In this blog post, we are going to cover a strategy to help you get a job as a pentester or application security professional.
There is a lot of content on what you need to learn but not that much on what strategy you should follow.
First, let’s say we have different levels of knowledge: level 0 to level 5. It is a totally arbitrary scale but I just want to illustrate my point.
Level 0 you know as much as anyone else who doesn’t work in security
Level 1 you know a bit more than the average person. You know some of the acronyms and can explain basic concepts. That is also the level where you should be careful as you feel like you know a lot but you’re just at the beginning of your journey
Level 2 is you can find bugs using automated tools or by just re-using payload and spamming every field in a page. At this level, if your tool doesn’t report an issue, you think there is no issue.
Level 3 is you are able to edit tools to change their behaviour, read a bit of code to understand what a tool is doing. You know how to debug a payload that doesn’t work.
Level 4 you are able to write advanced tools, derive new payloads and find bugs no one else found before.
Level 5 you master the domain. You publish bleeding edge research on the subject. Maybe did a talk at BlackHat on the subject or something.
It’s very simple to go from level 0 to level 1. It is a bit harder to go from level 1 to level 2. A lot harder to go from 2 to 3. Even harder to jump from 3 to 4 and going to 4 to 5 is extremely hard.
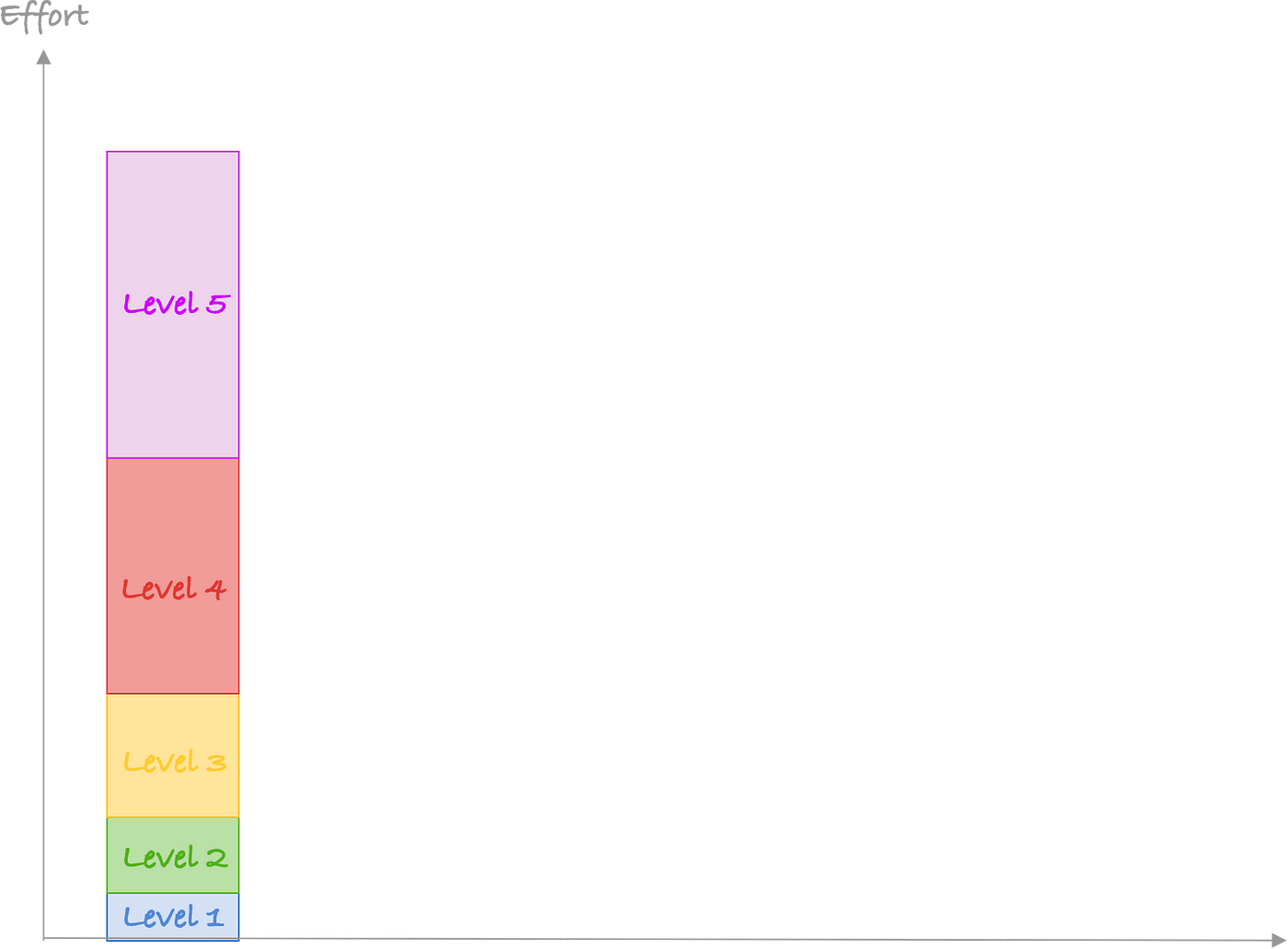
As a side note, the interesting thing is that most people even in security have a hard time telling the difference between 3 and 4 and they can’t tell the difference between 4 and 5 aside from “this person did a talk at BlackHat”.
Now let’s look at categories. Again completely arbitrary. Let’s divide pentest into the following categories:
- Network
- Web
- Exploitation
- Windows
- Unix/Linux
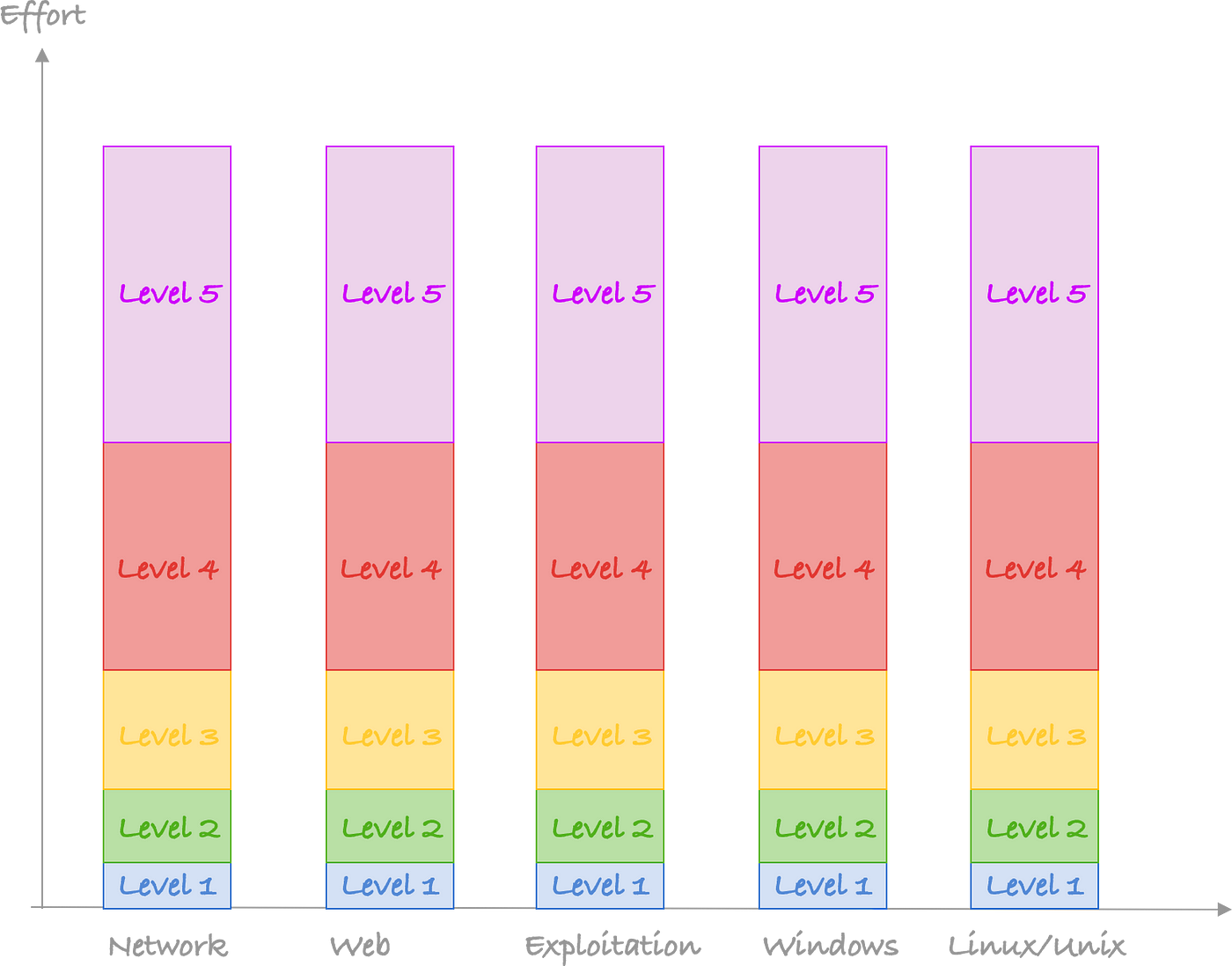
Now when you look at someone you admire in the industry, you feel like they are something like:
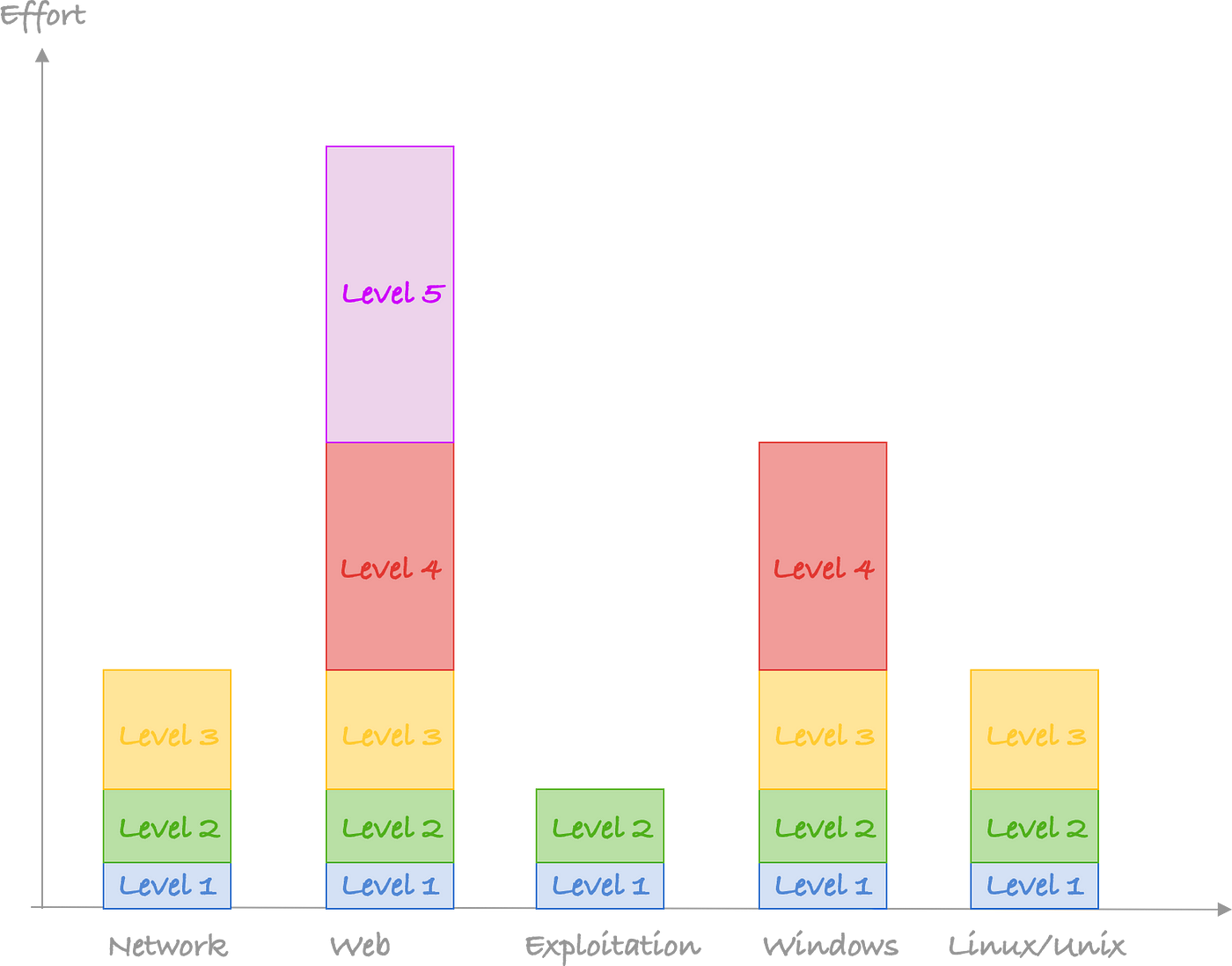
In reality, they are more like (and that is for the best of the best):
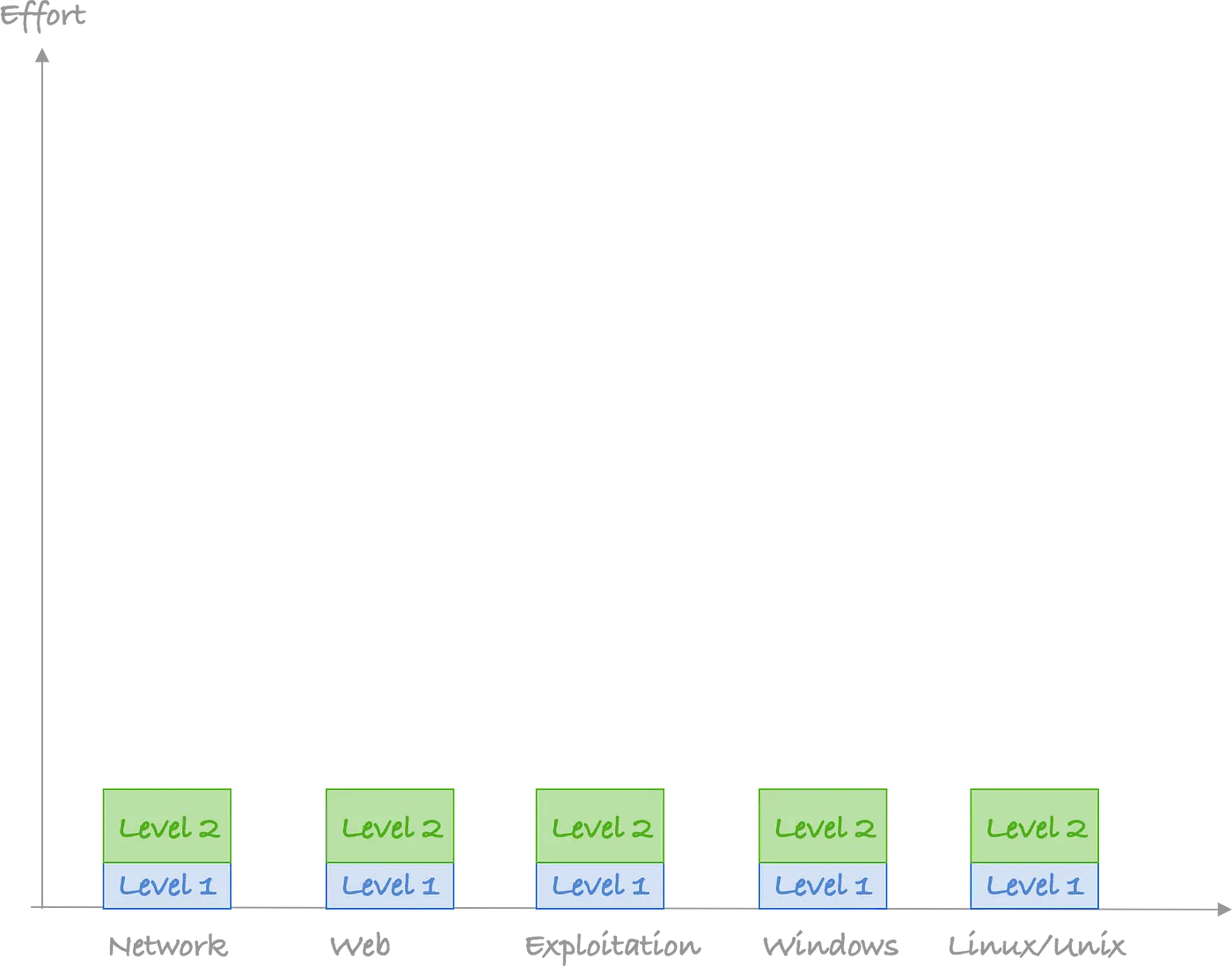
Now let’s see how a lot of people learn pentest or appsec when they get started. Most people go level 1 in one category, level 1 in another, then level 1 across the board. They look a bit like this:

Then they move to level 2, level 2 in one category, level 2 in another category and they keep going:
But then they hit a wall when they want to get to level 3 and often look at other level 2 they should learn that are adjacent to pentesting. Maybe a bit of social engineering, maybe a bit of programming:
The problem is that they never reach that level 3. Level 3 is where you start to really doing interesting things like writing/reading simple code, debugging complex issues, questioning the output of tools, being able to give useful advice to others. You also have all these intra key-skills that will help you get into level 3 in other domains:
- Being able to google things properly.
- Actually reading error messages.
- Not trusting the recommendations with the most votes on StackOverflow.
- Using tools like docker.
- Increase in velocity.
- Deep understanding of complex subjects
- Ability to comprehend trade-offs you may have to make.
- You know what you don’t know.
- ...
Now, let’s jump to the role of a team manager. When you are hiring juniors, you know that you’re not hiring the best pentesters. You are hiring the person who may become a great pentester. And you know (hopefully), that the hard part is not being a level 2 everywhere, it’s being able to become a level 3. You want junior who can demonstrate they managed to reach that level in one given field. Not necessarily across the field, just a subject in the field. But you are convinced that they are going to get there.
The team manager already have some people in their team. If you look at their team it might look something like this:
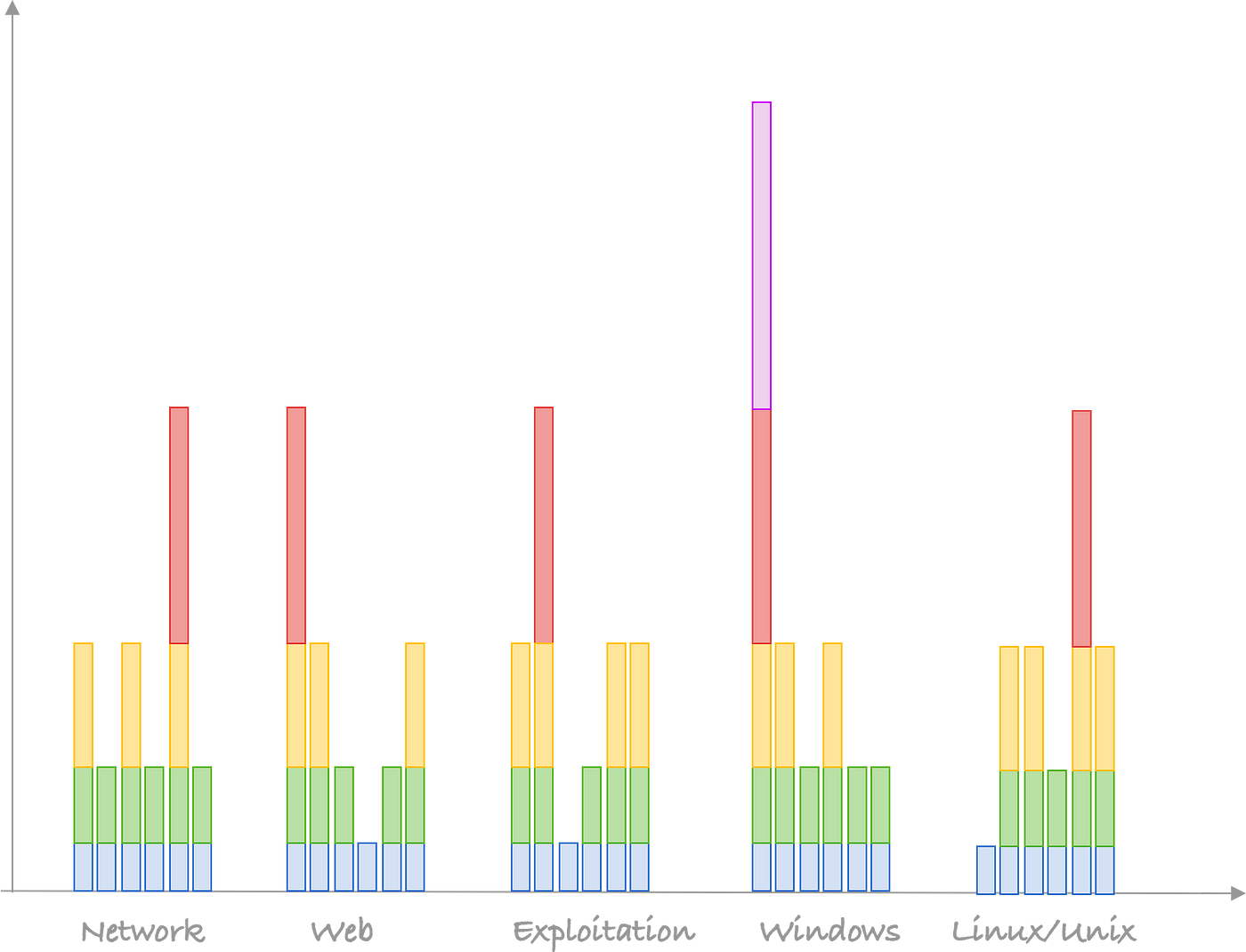
One person is level 2 across the board, that may be the manager. Then you have people who are level 2 and one level 3, or even level 4 and 5 if you are lucky.
The magic is that if you get your team working together, you get to have a team that can work in all categories at level 3 or 4.
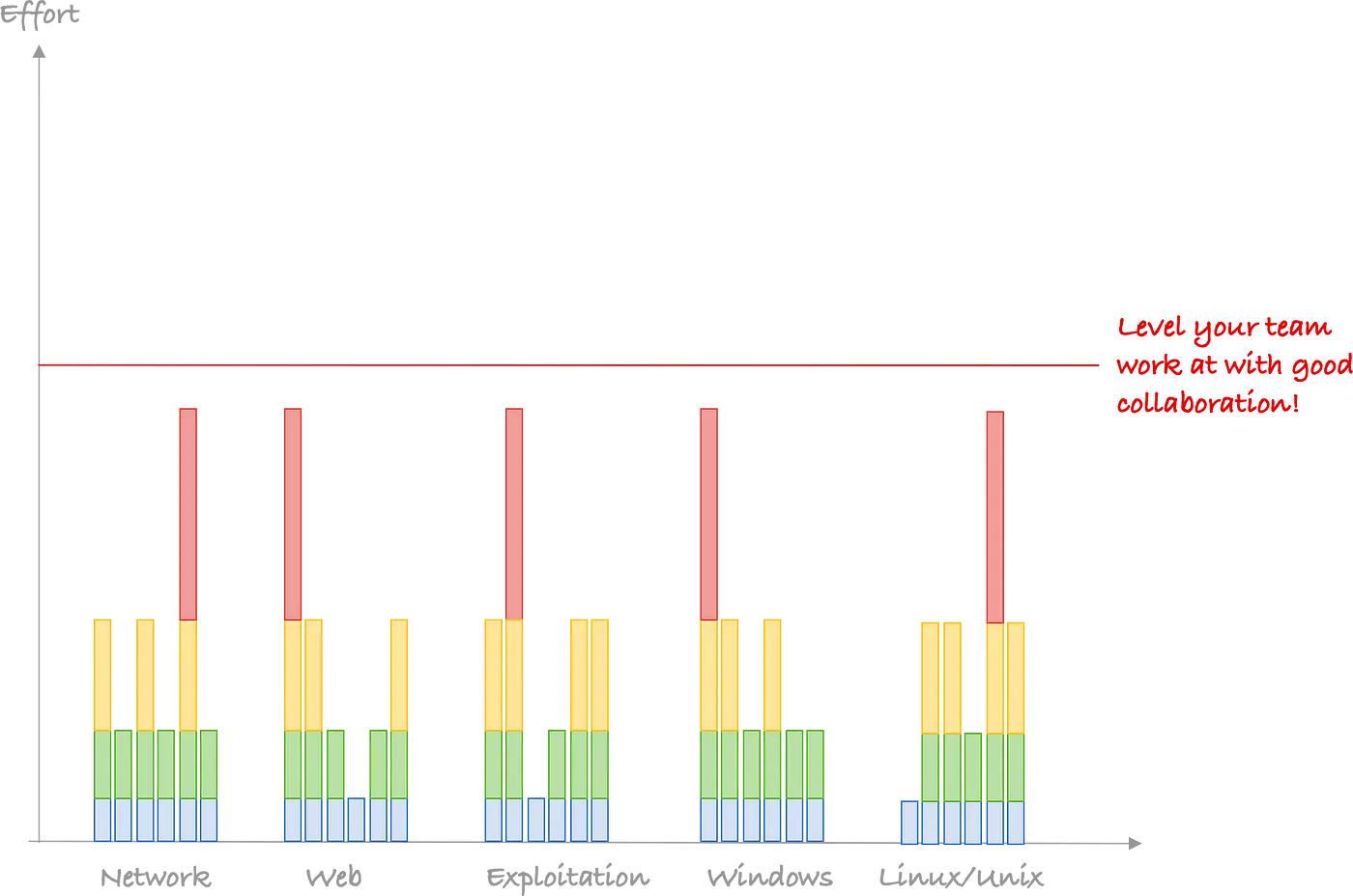
If you are hiring, you also know that a lot of people make it to level 2. But not so many people go to level 3, 4 or 5. And you know that level 3, 4 or 5 in one category with blind spots is a lot better than level 2 across the board. Level 3 gives you shells other people may miss, level 3 gives you talks at local meetups, level 3 gives you cross-pollination as in your whole team getting better in a subject thanks to that one person.
Down the track, your team will hopefully look like this:
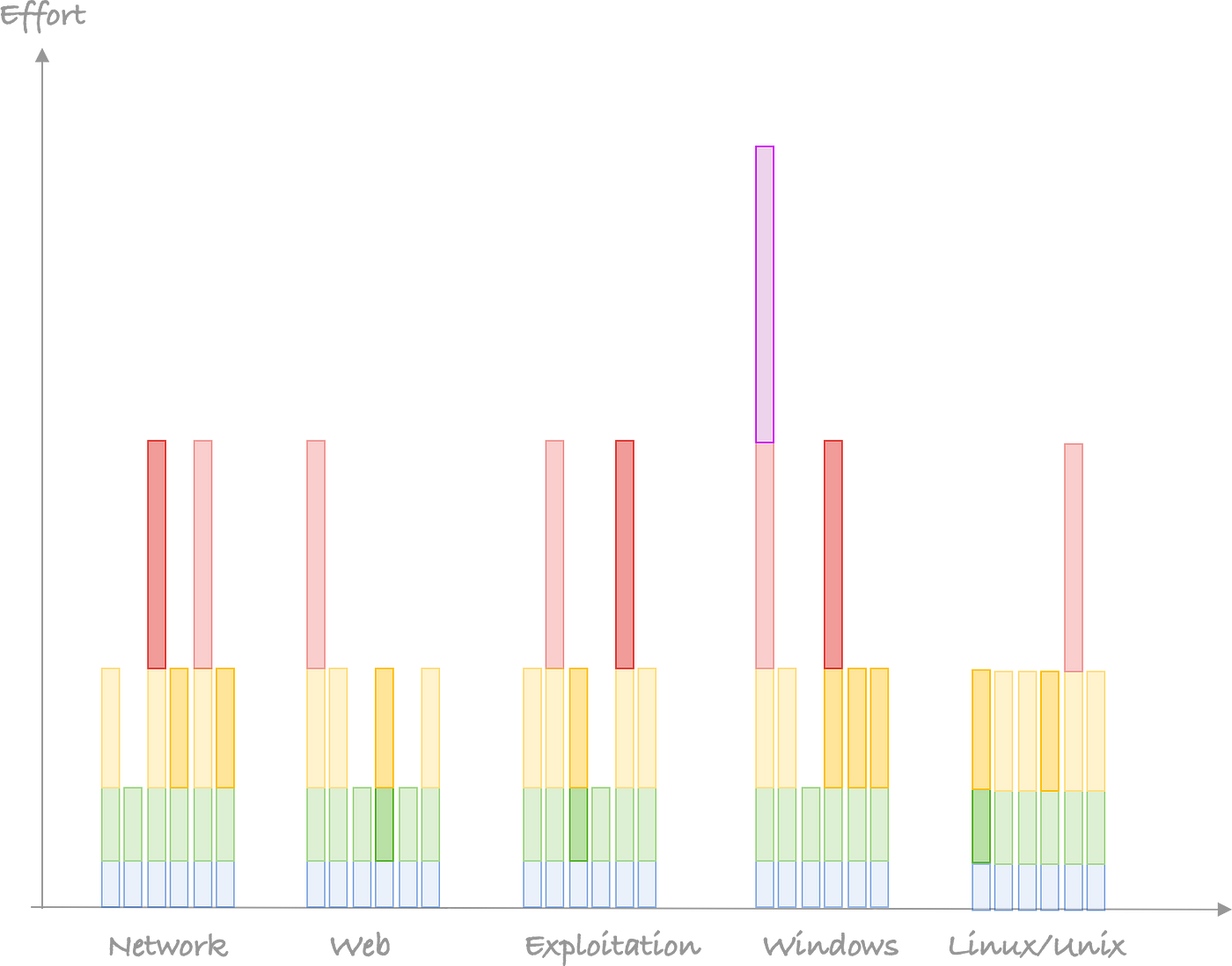
So let’s get back to you looking for a job, you would be better be a level 3 in one category instead of level 2 everywhere.
You may say: “Being level 3 in one category is incredibly hard!” And you will be right! My advice is first to focus your time in one category and get to level 2. Then find one subject in this category in which you want to go deep. Stick to this subject until you can understand and reproduce bleeding-edge research. Stick to it until you can debug tools for it. Stick to it until you can read the source code of tools for it. Stick to it until you can talk about it at a local meetup. Stick to it until you can do some write-ups on it. Basically, stick to it until people feel you’re really good at it. And then move to another subject in the same category.
Since a lot of work in pentesting is performing web testing and that a lot of people prefer to do internal testing (since it is like shooting fishes in a barrel). This is what most people should aim for:
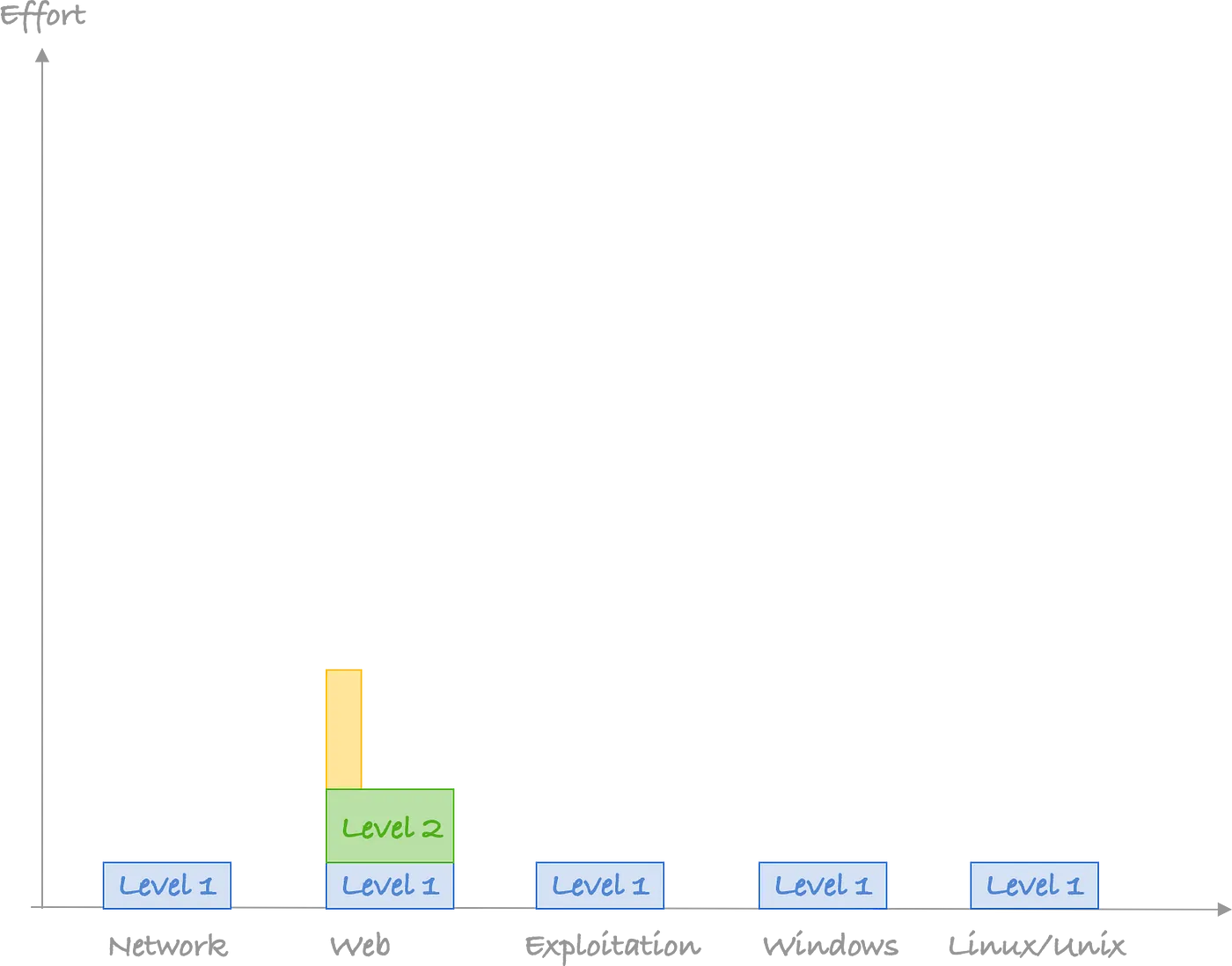
But don’t make the same mistake too many people are doing: trying to fix your blind spots instead of building on your strength. If you’re a developer, pick something that is related to code. If you are a Windows sysadmin, pick something that is related to Windows security…
To conclude, try to get really good at something instead of average at everything. This is where the bugs are and this is what will help you get a job.
